close
1. Install OpenSSL Toolkit (OpenSSL toolkit absolute path: $openssl_dir)
# tar zxvf openssl-1.0.1e.tar.gz
# cd openssl-1.0.1e
# ./config
# make
2. Create working directories (working directory absolute path: /ca_path)
# mkdir ca_path
# cd /ca_path
# mkdir rootCA signedCA
# cd rootCA
# mkdir certs crl newcerts private
# echo "01" > serial
# touch index.txt
# openssl rand 2048 > ./private/.rand
# chmod 600 ./private/.rand
# cp $openssl_dir/app/openssl.cnf /ca_path/openssl.cnf
3. Modify $ca_path/openssl.cnf
[Before] dir = ./demoCA # Where everything is kept
[After] dir = /ca_path/rootCA # Where everything is kept
4. Generate Root CA
# cd /ca_path/rootCA
# openssl req -new -x509 -newkey rsa:2048 -keyout private/cakey.pem -out cacert.pem -days 3650 -config /ca_path/openssl.cnf
Generating a 2048 bit RSA private key
… (skip)
Enter PEM pass phrase: please enter password
Verifying - Enter PEM pass phrase: please enter password again
… (skip)
Country Name (2 letter code) [AU]: TW
State or Province Name (full name) [Some-State]: Taiwan
Locality Name (eg, city) []: Taoyuan
Organization Name (eg, company) [Internet Widgits Pty Ltd]: Ingrasys
Organizational Unit Name (eg, section) []: FDD
Common Name (e.g. server FQDN or YOUR name) []: ROOT CA
Email Address []: ssl@ingrasys.com
-newkey rsa:nbits creates a new certificate request and a new private key, and generates an RSA key nbits in size
-days arg the number of days to certify the certificate for
5. Sign a new certificate from Root CA
# cd /ca_path/signedCA
# openssl req -nodes -new -x509 -newkey rsa:2048 -keyout mykey.pem -out myreq.pem -days 365 -config /ca_path/openssl.cnf
Generating a 2048 bit RSA private key
… (skip)
Country Name (2 letter code) [AU]: TW
State or Province Name (full name) [Some-State]: Taiwan
Locality Name (eg, city) []: Taoyuan
Organization Name (eg, company) [Internet Widgits Pty Ltd]: Ingrasys
Organizational Unit Name (eg, section) []: FDD
Common Name (e.g. server FQDN or YOUR name) []: 192.168.54.151 //Card IP address
Email Address []: ssl@ingrasys.com
# openssl x509 -x509toreq -in myreq.pem -signkey mykey.pem -out tmp.pem
# openssl ca -config /ca_path/openssl.cnf -policy policy_anything -out mycert.pem -infiles tmp.pem
Enter pass phrase for /ca_path/rootCA/private/cakey.pem: please enter password set in Step.4
… (skip)
Sign the certificate? [y/n]: y
out of 1 certificate requests certified, commit? [y/n] y
6. Upload SSL certificate to Baboon
A. Creating a new mini_httpd.pem
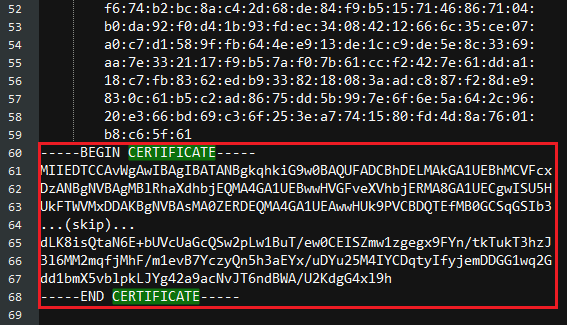
Open /ca_path/signedCA/mycert.pem with a text editor and copy the contents between “-----BEGIN CERTIFICATE-----“ and “-----END CERTIFICATE-----“
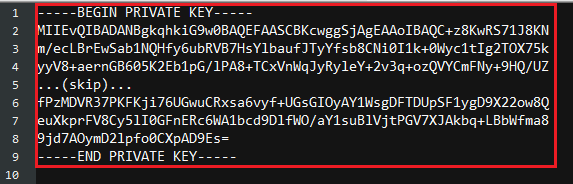
Open /ca_path/signedCA/mykey.pem with a text editor and copy the contents between “-----BEGIN PRIVATE KEY-----“ and “-----END PRIVATE KEY-----“
Create a new file named mini_httpd.pem and paste these two paragraphs onto it.
B. Upload mini_httpd.pem to Baboon
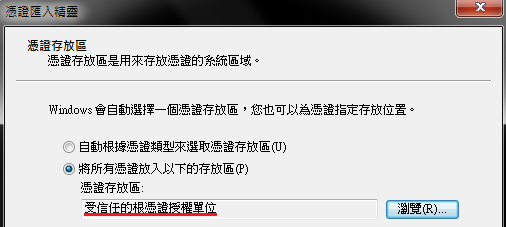
7. Import Root CA to system
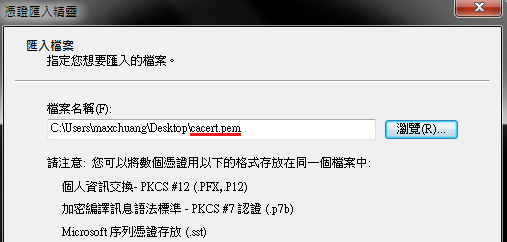
A. Download /ca_path/rootCA/cacert.pem to PC
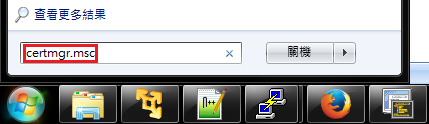
B. Execute “certmgr.msc”
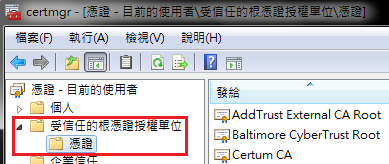
C.
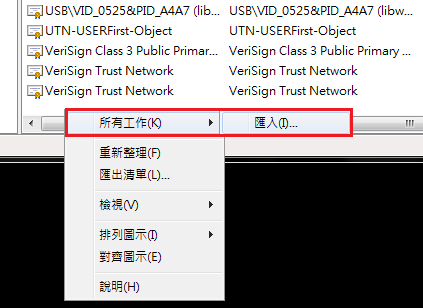
D. Right-click in the right pane and choose 'All Tasks' then 'Import…'
E. Import “cacert.pem”
F.
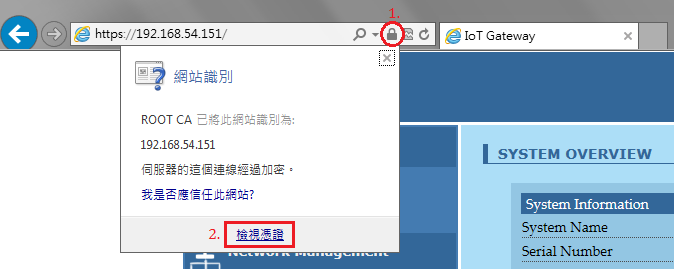
8. Validate uploaded CA correctness
Are all attributes identical with the settings in Step.5?
文章標籤
全站熱搜





 留言列表
留言列表
